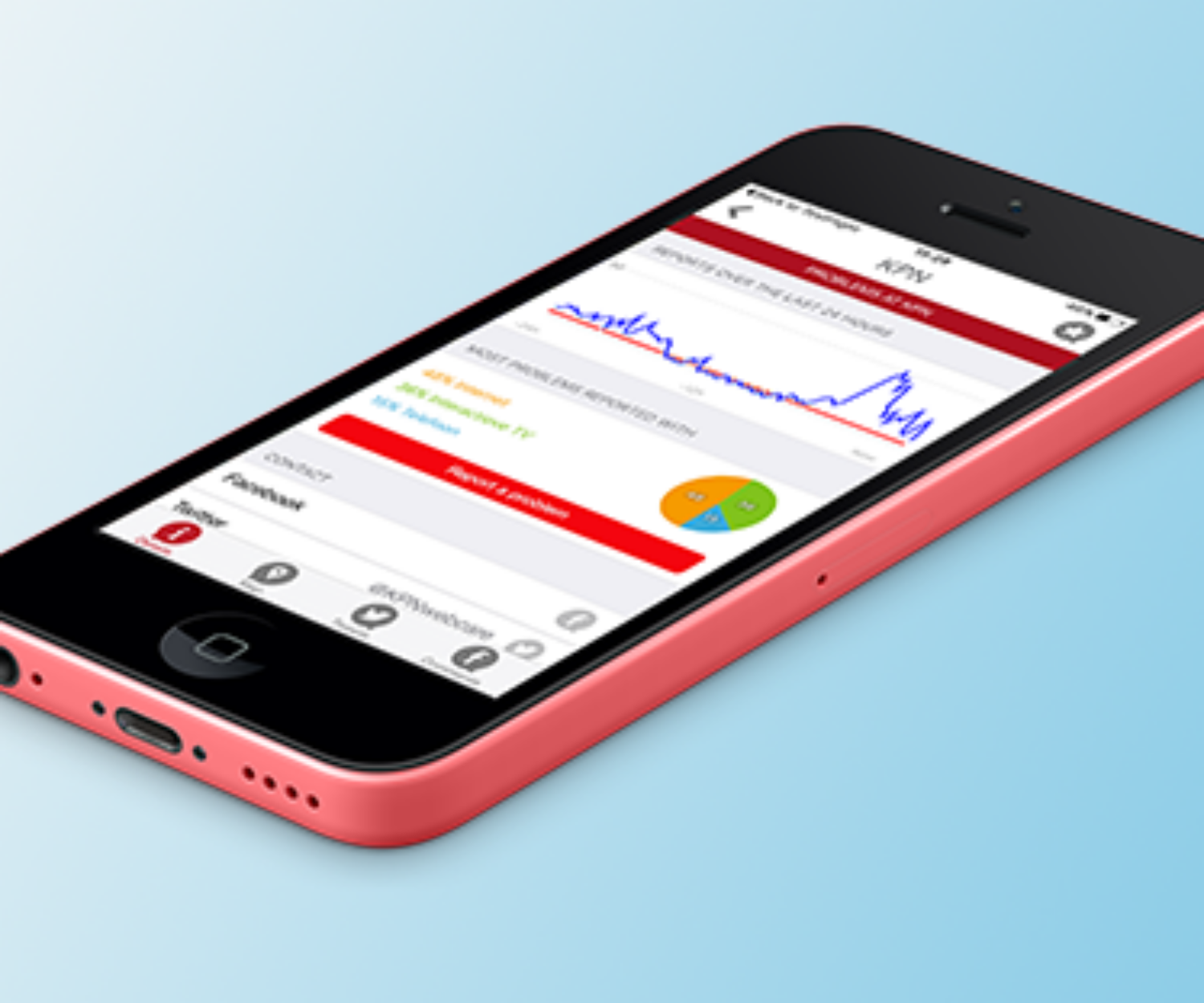
The banking industry is facing a big challenge. It's related to technological advancements and how they continuously alter consumer behavior.…
CONTACT US
Give us a call or drop us a line if you are looking for a painless, affordable and quick mobile application and/or web development.
Netherlands Office
1412 KA, Naarden
Amersfoortsestraatweg 7
The Netherlands
+31 (0)6410 475 80
Bulgaria Office
4 Danail Nikolaev str.
4000, Plovdiv
Bulgaria
+359 (0)877 652 620
Black Bear
© 2012 – 2025 Black Bear Solutions BV